使用cfssl创建kubeconfig文件为kubernetes认证授权
RBAC基础 *
目的为开发人员访问使用kubectl做身份进行认证和对其权限做出限制。步骤和部署k8s时候创建admin一样只是绑定权限不一样而已
创建一个devuser用户并且给对应的命名空间所有权限
1、安装CFSSL:
http://pkg.cfssl.org/
curl -s -L -o /bin/cfssl https://pkg.cfssl.org/R1.2/cfssl_linux-amd64
curl -s -L -o /bin/cfssljson https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64
curl -s -L -o /bin/cfssl-certinfo https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64
chmod +x /bin/cfssl*创建 CA 证书和秘钥
生成ca配置:如果没有ca-config.json
cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF创建 dev-user-csr.json 文件
默认生成 证书CN名称为账号名称
cfssl print-defaults csr > devuser-csr.json 修改
{
"CN": "devuser",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}切换到/etc/kubernetes/ssl目录下面确保目录下面包含以下文件
ca-key.pem ca.pem ca-config.json devuser-csr.json[root@dev-k8s-m1 ssl]# cfssl gencert -ca=kube-ca.pem -ca-key=kube-ca-key.pem -config=ca-config.json -profile=kubernetes dev-user-csr.json | cfssljson -bare devuser查看生成的文件
[root@dev-k8s-m1 ssl]# ls devuser*
devuser.csr devuser-key.pem devuser.pem创建 kubeconfig 文件
# 设置集群参数
export KUBE_APISERVER="https://172.20.0.113:6443"
kubectl config set-cluster kubernetes \
--certificate-authority=/etc/kubernetes/ssl/ca.pem \
--embed-certs=true \
--server=${KUBE_APISERVER} \
--kubeconfig=devuser.kubeconfig
# 设置客户端认证参数
kubectl config set-credentials devuser \
--client-certificate=/etc/kubernetes/ssl/devuser.pem \
--client-key=/etc/kubernetes/ssl/devuser-key.pem \
--embed-certs=true \
--kubeconfig=devuser.kubeconfig
# 设置上下文参数
kubectl config set-context kubernetes \
--cluster=kubernetes \
--user=devuser \
--namespace=dev \
--kubeconfig=devuser.kubeconfig
# 设置默认上下文
kubectl config use-context kubernetes --kubeconfig=devuser.kubeconfig至此证书和kubeconfig文件完成 devuser.kubeconfig文件就是/root/.kube/config文件 但是k8s还没有对应的用户和权限
RoleBinding
通过 RBAC创建角色绑定以将该用户的限制在某个或某几个 namespace 空间范围内,例如:
[root@dev-k8s-m1 ssl]# kubectl create rolebinding devuser-admin-binding --clusterrole=admin --user=devuser --namespace=dev
rolebinding.rbac.authorization.k8s.io/devuser-admin-binding created
[root@dev-k8s-m1 ssl]# kubectl create rolebinding devuser-admin-binding --clusterrole=admin --user=devuser --namespace=sit1
rolebinding.rbac.authorization.k8s.io/devuser-admin-binding created
[root@dev-k8s-m1 ssl]# kubectl create rolebinding devuser-admin-binding --clusterrole=admin --user=devuser --namespace=sit2
rolebinding.rbac.authorization.k8s.io/devuser-admin-binding created
[root@dev-k8s-m1 ssl]# kubectl create rolebinding devuser-admin-binding --clusterrole=admin --user=devuser --namespace=istio-test
rolebinding.rbac.authorization.k8s.io/devuser-admin-binding created
[root@dev-k8s-m1 ssl]# kubectl create rolebinding devuser-admin-binding --clusterrole=admin --user=devuser --namespace=istio-uat
rolebinding.rbac.authorization.k8s.io/devuser-admin-binding created
[root@dev-k8s-m1 ssl]# kubectl create rolebinding devuser-admin-binding --clusterrole=admin --user=devuser --namespace=istio-dev
rolebinding.rbac.authorization.k8s.io/devuser-admin-binding created
[root@dev-k8s-m1 ssl]# kubectl create rolebinding devuser-admin-binding --clusterrole=admin --user=devuser --namespace=uat
rolebinding.rbac.authorization.k8s.io/devuser-admin-binding created
验证
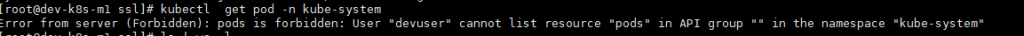
如果通过eip连接会提示如下错误因为ca证书没有添加eip
Unable to connect to the server: x509: certificate is valid for 192.168.x.x, 127.0.0.1, 10.43.0.1, not 119.x.x.x
解决方法不要验证证书安全性
kubectl -insecure-skip-tls-verify
或者
config添加
- cluster:
server: https://119.x.x.x:6443
insecure-skip-tls-verify: true
name: kubernetes给dashboard创建一个只读角色权限
kubectl create serviceaccount dashboard-read -n kube-system
kubectl create clusterrolebinding dashboard-read -n kube-system --clusterrole=view --serviceaccount=kube-system:dashboard-read
kubectl get secret $(kubectl get serviceaccount dashboard-read -n kube-system -o jsonpath="{.secrets[0].name}") -o jsonpath="{.data.token}" -n kube-system | base64 --decode

