使用 LetsEncrypt配置kubernetes ingress-nginx免费HTTPS证书

使用Helm安装
作为上面提到的YAML清单的替代方案,我们还提供了用于安装cert-manager的官方Helm图表。
curl -s -o helm.tar.gz https://storage.googleapis.com/kubernetes-helm/helm-v2.12.1-linux-amd64.tar.gz \
&& tar -zxvf helm.tar.gz \
&& cp -p -f linux-amd64/helm /usr/local/bin/ \
&& helm initcat <<EOF | kubectl apply -f -
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: tiller
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: tiller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: tiller
namespace: kube-system
EOF
helm init --service-account tiller --upgrade步骤
要安装Helm图表,您必须运行:
# Install the CustomResourceDefinition resources separately
kubectl apply -f https://raw.githubusercontent.com/jetstack/cert-manager/release-0.8/deploy/manifests/00-crds.yaml
# Create the namespace for cert-manager
kubectl create namespace cert-manager
# Label the cert-manager namespace to disable resource validation
kubectl label namespace cert-manager certmanager.k8s.io/disable-validation=true
# Add the Jetstack Helm repository
helm repo add jetstack https://charts.jetstack.io
# Update your local Helm chart repository cache
helm repo update
# Install the cert-manager Helm chart
helm install \
--name cert-manager \
--namespace cert-manager \
--version v0.8.1 \
jetstack/cert-manager默认的cert-manager配置适用于大多数用户,但可以在Helm chart README中找到可用选项的完整列表。
验证安装
安装cert-manager后,可以通过检查cert-manager运行pod 的命名空间来验证它是否已正确部署:
kubectl get pods --namespace cert-manager
NAME READY STATUS RESTARTS AGE
cert-manager-5c6866597-zw7kh 1/1 Running 0 2m
webhook-78fb756679-9bsmf 1/1 Running 0 2m
webhook-ca-sync-1543708620-n82gj 0/1 Completed 0 1m开始为Ingress主机颁发证书
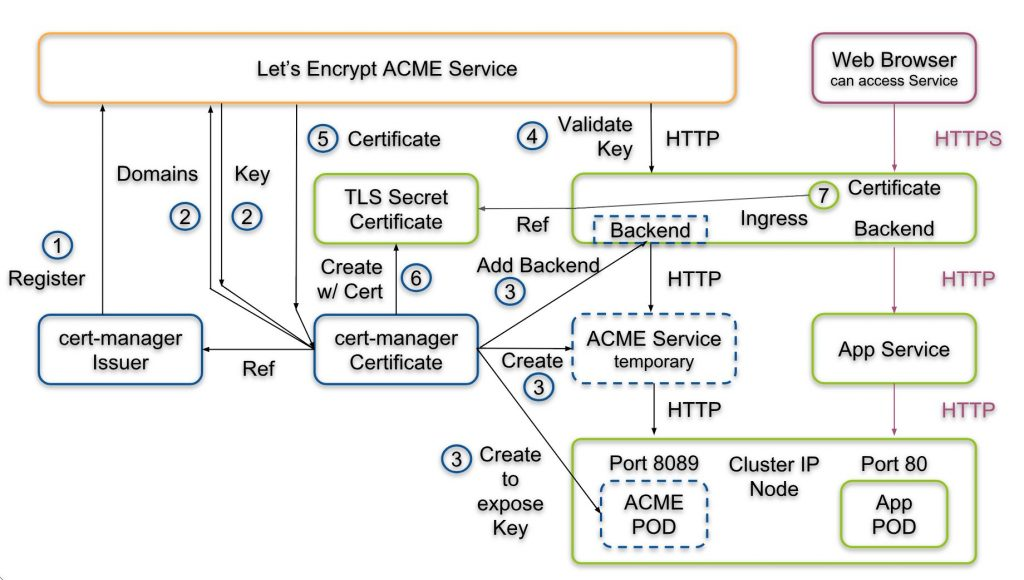
k8s提供Issuer跟ClusterIssuer两种,前者是单一namespace使用,后者是cluster wide也就是每個namespace都可以reference到。 需要创建一个ClusterIssuer
更新cert-manager你需要配置一个缺缺省的 cluster issuer,当部署Cert manager的时候,用于支持 kubernetes.io/tls-acme: "true"annotation来自动化TLS:
helm upgrade cert-manager jetstack/cert-manager --namespace cert-manager --version v0.8.1 --set ingressShim.defaultIssuerName=letsencrypt-prod --set ingressShim.defaultIssuerKind=ClusterIssuer目前cert-manager支持ACME跟CA方式,而ACME又分DNS/HTTP两种
cat << EOF| kubectl create -n ingress -f -
apiVersion: certmanager.k8s.io/v1alpha1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
server: https://acme-v02.api.letsencrypt.org/directory
email: xxx@example.com
privateKeySecretRef:
name: letsencrypt-prod
http01: {}
EOF将以下内容添加到Ingress资源
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: jenkins
namespace: jenkins
annotations:
kubernetes.io/ingress.class: nginx
certmanager.k8s.io/cluster-issuer: letsencrypt-prod
kubernetes.io/tls-acme: "true"
#certmanager.k8s.io/acme-challenge-type: "dns01"
spec:
tls:
- hosts:
- jenkins.example.com
secretName: letsencrypt-prod
rules:
- host: jenkins.example.com
http:
paths:
- backend:
serviceName: jenkins
servicePort: 808
- host: xxx.example.com
http:
paths:
- backend:
serviceName: xxx
servicePort: 80kubectl describe certificate letsencrypt-prod


